How it works
Honeypot’s intention is to trap malware by exploiting vulnerabilities exposed by services offered to a network, the ultimate goal is to gain a copy of the malware.
Security
As Software is likely to have bugs, bugs in software offering network services can be exploitable, and dionaea is software offering network services, it is likely dionaea has exploitable bugs.
To be able to run certain actions which require privileges, after dionaea dropped them, dionaea creates a child process at startup and asks the child process to run actions that require elevated privileges. This does not guarantee anything, but it should be harder to get gain root access to the system from an unprivileged user in a chroot environment.
Network Connectivity
Given the software’s intended use, a network is crucial. All network is within the main process in a so-called non-blocking manner. To understand nonblocking, imagine you have many pipes in front of you, and these pipes can send you something, and you can put something into the pipe. If you want to put something into a pipe, while it is crowded, you’d have to wait, if you want to get something from a pipe, and there is nothing, you’d have to wait too. Doing this pipe game non-blocking means you won’t wait for the pipes to be written/readable, you’ll get something off the pipes once data arrives, and write once the pipe is not crowded. If you want to write a large chunk to the pipe, and the pipe is crowded after a small piece, you note the rest of the chunk you wanted to write and wait for the pipe to get ready.
DNS resolves are done using libudns, which is a neat non-blocking dns resolving library with support for AAAA records and chained cnames. So much about non-blocking.
AWS dionaea uses libev to get notified once it can act on a socket, read or write.
AWS dionaea can offer services via tcp/udp and tls for IPv4 and IPv6, and can apply rate limiting and accounting limits per connections to tcp and tls connections — if required.
Solution Overview:
- This cloud formation template is deployed in ECS fargate.
- Due to the docker approach, the solution is very light weight and the template makes the deployment process also very easy.
- The elastic search credentials are passed during the stack creations, using which the indexes are created and the logs are stored in the elastic search.
- Other network-related configurations can also be defined in the cloud formation template.
Git Repo: https://github.com/kkpkishan/dionaea.git
Steps:
Create dionaea automation using CloudFormation.
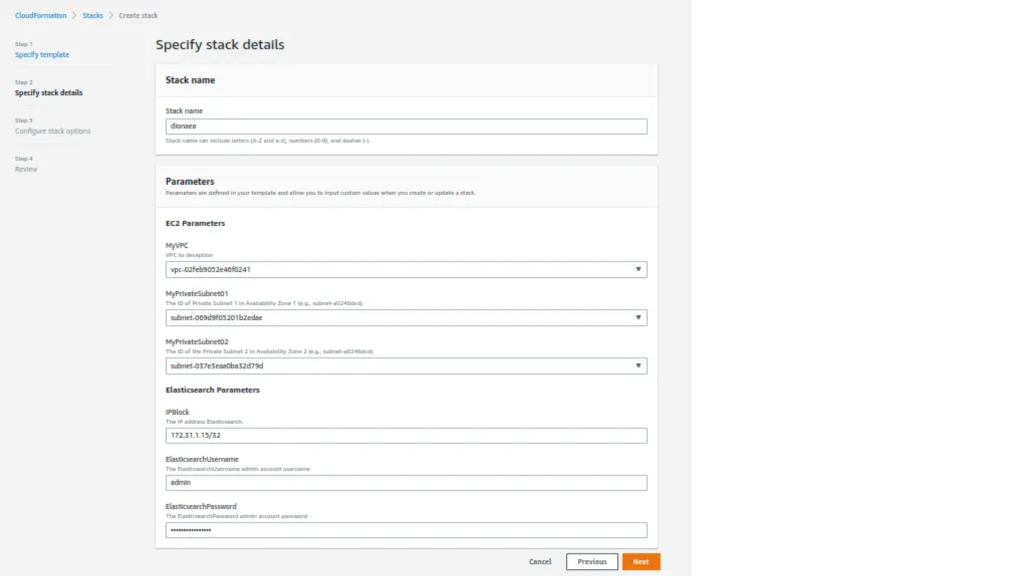
List of AWS resources that will be created by this cloud formation template:
- ECS Fargate cluster
- Task execution role
- Security Group
- Task definition
- ECS Service