AWS WAF is a web application firewall that lets you monitor the HTTP and HTTPS requests that are forwarded to Amazon CloudFront or an Application Load Balancer. AWS WAF also lets you control access to your content.
- Allow all requests except the ones that you specify – This is useful when you want CloudFront or an Application Load Balancer to serve content for a public website, but you also want to block requests from attackers.
- Block all requests except the ones that you specify – This is useful when you want to serve content for a restricted website whose users are readily identifiable by properties in web requests, such as the IP addresses that they use to browse to the website.
- Count the requests that match the properties that you specify – When you want to allow or block requests based on new properties in web requests, you first can configure AWS WAF to count the requests that match those properties without allowing or blocking those requests. This lets you confirm that you didn’t accidentally configure AWS WAF to block all the traffic to your website.
Using AWS WAF has several benefits:
- Additional protection against web attacks using conditions that you specify. You can define conditions by using characteristics of web requests such as the following:
- IP addresses that requests originate from.
- Country that requests originate from.
- Values in request headers.
- Strings that appear in requests, either specific strings or string that match regular expression (regex) patterns.
- Length of requests.
- Presence of SQL code that is likely to be malicious (known as SQL injection)
- Presence of a script that is likely to be malicious (known as cross-site scripting).
- Rules that can allow, block or count web requests that meet the specified conditions. Alternatively,rules can block or count web requests that not only meet the specified conditions,but also exceed a specified number of requests in any 5-minute period.
- Rules that you can reuse for multiple web applications.
- Real-time metrics and sampled web requests.
- Automated administration using the AWS WAF API.
The Basic components of the WAF are :
- Conditions :
Conditions define the basic characteristics that you want AWS WAF to watch for in web requests:
- Scripts that are likely to be malicious. Attackers embed scripts that can exploit vulnerabilities in web applications. This is known as cross-site scripting.
- IP addresses or address ranges that requests originate from.
- Country or geographical location that requests originate from.
- Length of specified parts of the request, such as the query string.
- SQL code that is likely to be malicious. Attackers try to extract data from your database by embedding malicious SQL code in a web request. This is known as SQL injection.
- Strings that appear in the request, for example, values that appear in the User-Agent header or text strings that appear in the query string.
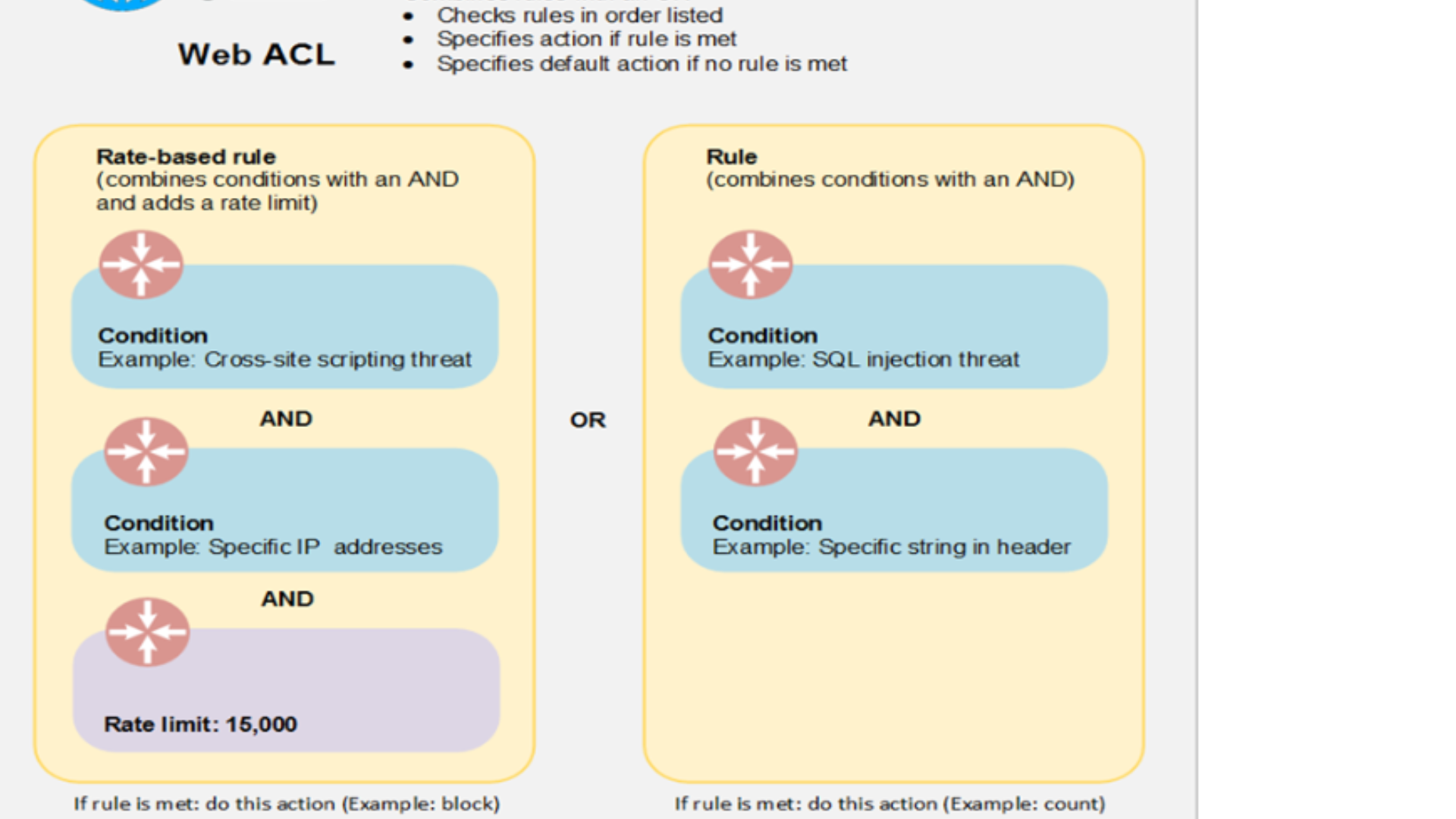
2. Rules :
You combine conditions into rules to precisely target the requests that you want to allow, block, or count. AWS WAF provides two types of rules:
Regular rule
Regular rules use only conditions to target specific requests. For example, based on recent requests that you’ve seen from an attacker.
Rate-based rule:
Rate-based rules are similar to regular rules, with one addition: a rate limit. Rate-based rules count the requests that arrive from a specified IP address every five minutes. The rule can trigger an action if the number of requests exceed the rate limit.
Web ACLs :
- After you combine your conditions into rules, you combine the rules into a web ACL. This is where you define an action for each rule—allow, block, or count—and a default action
- When a web request matches all the conditions in a rule, AWS WAF can either block the equest or allow the request to be forwarded to CloudFront or an Application Load Balancer. You specify the action that you want AWS WAF to perform for each ru.