About Customer:
A leading India-based manufacturing firm providing the highest quality Non Ferrous Electrical Connectors, Electrical Sub-Assemblies, Complete Product Assemblies and Brand Labelled Products.
With over 40+ years of experience and a wide array of state-of-the-art manufacturing technologies, the Company has become the trusted partner and Tier-1 supplier to major electrical firms in the European and North American markets. Their exceptional service alongside reliable and cost-effective components allows them to exceed their customer’s expectations time and time again.
Challenges:
As per our customer’s need analysis and discussions we identified the following requirements.
- Migrate the Odoo ERP system to AWS with minimal disruption.
- Security Compliance:
- Adherence to industry-standard compliance regulations, such as ISO 9000, ISO 27000
- Implementation of robust security measures and services like Security Hub, Config, GuardDuty, CloudWatch, and CloudTrail
- Scalability:
- Vertical scalability to accommodate growing business needs and customer demands
- Ability to scale resources and infrastructure seamlessly and efficiently
- Resource Monitoring:
- Comprehensive monitoring and tracking of cloud resources and server resources
- Real-time visibility into resource usage and performance metrics
- Reliability and Data Protection:
- High reliability and availability of services and products
- Robust backup and easy restore capabilities for data integrity and business continuity
- Cost-effectiveness:
- Provision of reliable and cost-effective components and solutions
- Optimization of resource utilization and cost management
- Global Reach:
- Established presence and customer base in European and North American markets
- Ability to cater to international customers and meet their specific requirements
These requirements encompass the key aspects of security, compliance, scalability, monitoring, reliability, cost-effectiveness, and global reach, as highlighted in the provided information.1
Proposed Solution
The key advantages of AWS Cloud computing specific to this customer is summarized as follows:
Secure Access: AWS Systems Manager provides secure remote access to instances without opening inbound ports or managing SSH keys, with centralized access control and auditing.
Built-in Monitoring: AWS CloudWatch provides monitoring for CPU, memory, disk, network, etc. at negligible cost, including critical alarm triggers.
Elastic Block Storage (EBS): EBS volumes can dynamically increase size, modify IOPS, and change volume type on live production volumes. They provide high data durability and availability with automatic replication across multiple servers.
High Availability: AWS services offer high availability, typically around 99.95%.
Security Features: AWS provides free SSL/TLS certificates, data encryption at rest, detailed logging with CloudTrail, and fine-grained access control with IAM.
Scalability: Horizontal scaling is easy with Auto Scaling Groups, and vertical scaling can be achieved by resizing instances.
Backup and Archival: EBS snapshots and S3 provide highly durable and automated backup and archival solutions.
Pay-as-you-go Model: AWS allows you to pay only for the resources you use, scaling up or down as needed.
Architecture Diagram
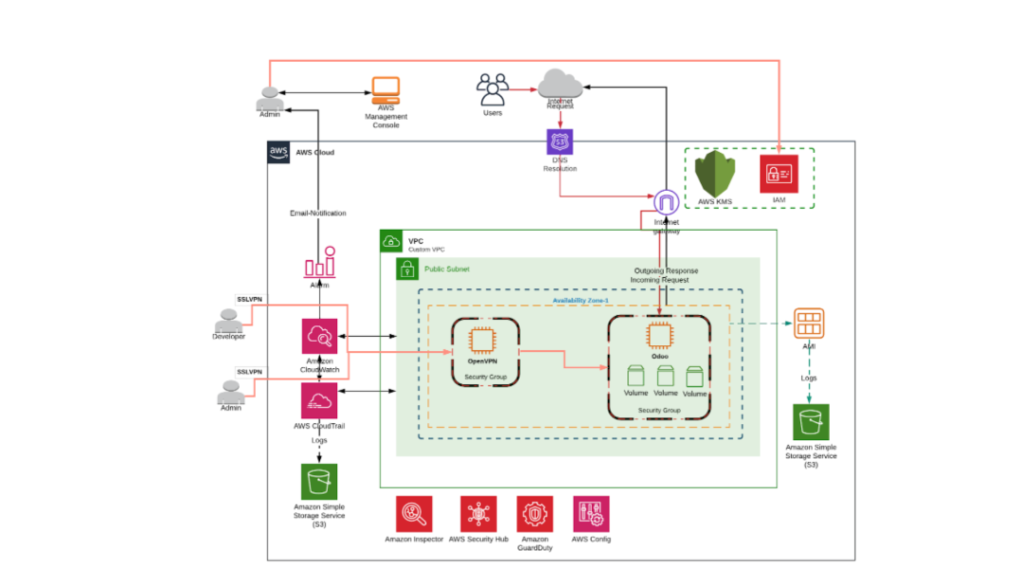
AWS Service Used and the purpose of the services
AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is a web service that helps us to set up secure control access to AWS resources. It allows our client to create and manage AWS users and groups, and use permissions to grant or deny their access to AWS service resources. IAM enabled our client to follow security best practices, such as least privilege access and multi-factor authentication (MFA), by providing granular control over who can access which resources and under what conditions. It is a foundational service for securely managing access to AWS resources, ensuring that only authorised users and applications can access and operate on AWS assets. MFA is the default policy for secure user login.
CloudTrail :
AWS CloudTrail is a service that enables governance, compliance, and operational auditing of AWS account. It provides a record of actions taken by any entity (user, role, or AWS service) that performs activities in the AWS environment. CloudTrail captures API calls and related events, including the identity of the caller, the time of the call, the request parameters, and the response elements. This audit trail allows the auditor to monitor and analyze activity across the AWS infrastructure, enabling our client to meet compliance requirements, conduct security analysis, and identify potential security incidents or unauthorized access attempts. CloudTrail’s log files are now be stored securely in Amazon S3 buckets or streamed to other monitoring and analysis services, making it a crucial security and compliance tool for maintaining visibility and control over the AWS environment.
CloudWatch :
AWS CloudWatch is a monitoring and observability service that provides valuable security insights and capabilities for AWS resources and applications. It collects and tracks metrics, logs, and events from various AWS services, allowing the client to monitor and analyse operational performance, resource utilisation, and security-related activities. CloudWatch Logs can ingest and centralise log data from various sources, including security logs from services like AWS WAF, VPC Flow Logs, and AWS CloudTrail, enabling the client to detect and investigate potential security incidents or anomalies. Additionally, CloudWatch Alarms were configured to trigger notifications or automated actions based on predefined thresholds or patterns, helping in proactively responding to security-related events or deviations from expected behaviour. By integrating with other AWS security services like AWS Security Hub and AWS Config, CloudWatch plays a crucial role in providing visibility, alerting, and automated remediation capabilities, enhancing the overall security posture of the AWS environment.
EC2 :
AWS Elastic Compute Cloud (EC2) provides vertical scaling capabilities, which now allows our client to increase or decrease the compute resources (CPU, memory, storage) of an existing EC2 instance without having to provision a new instance or restart the existing one. This is particularly useful when the application’s resource requirements change over time, and the client needs to adjust the instance size accordingly.
Here’s how vertical scaling works with AWS EC2:
- Instance Types: AWS offers a wide range of instance types with varying combinations of CPU, memory, storage, and networking resources. Now our client can choose the appropriate instance type based on their application’s requirements.
- Resizing: We also helped our client to resize (vertically scale) an existing EC2 instance by changing its instance type. This process involved stopping the instance, modifying its instance type, and then starting it again. AWS does not charge for the downtime incurred during this process.
- Elastic Volumes: AWS EC2 instances use Elastic Block Store (EBS) volumes for persistent storage. When resizing an instance, we helped in setting up this feature and now our client can also modify the EBS volume size to accommodate their storage needs.
Vertical scaling with EC2 is particularly useful in scenarios where there is a monolithic application or a single-instance workload that requires more or fewer resources over time, as applicable in this case. It can help optimise resource utilisation and cost-effectiveness by allowing scale up or down the instance size as needed, without disrupting the application or requiring complex architectural changes.
However, it’s important to note that vertical scaling has limitations in terms of the maximum available resources within a single instance. If the application requires more resources beyond what a single instance can provide, horizontal scaling (adding or removing instances) may be a more appropriate approach. We informed and trained the resources at client organization to make note of this and deal with it accordingly.
Security Group :
An AWS Security Group is a virtual firewall that controls inbound and outbound traffic to and from Amazon Elastic Compute Cloud (EC2) instances. It acts as a fundamental security layer for EC2 instances, allowing it to specify rules that govern which traffic is permitted or denied based on protocols, ports, and source or destination IP addresses or IP address ranges.
AWS Inspector :
AWS Inspector is a vulnerability management service that helps to inspect AWS resources for potential security vulnerabilities and deviations from best practices. It automatically assesses applications deployed on AWS for exposure, vulnerabilities, and deviations from security best practices. Inspector performs network accessibility assessments and checks for unintended network access, as well as evaluates the EC2 instance software and operating system against known vulnerabilities. It provides detailed findings, including descriptions and remediation recommendations, to help prioritise and address identified vulnerabilities and security risks across AWS infrastructure.
AWS Config :
AWS Config is a service that enables us to assess, audit, and evaluate the configurations of the AWS resources. It continuously monitors and records configuration changes to the AWS resources and allows us to automate the evaluation of recorded configurations against desired configurations. This helped us to simplify compliance auditing, security analysis, change management, and operational troubleshooting. AWS Config provides a detailed view of the configuration of AWS resources in the account, including how they relate to one another and how they were configured in the past, enabling us to see how configurations and relationships change over time. It acts as a powerful tool for enforcing compliance with internal policies, industry standards, and regulatory requirements across this AWS infrastructure.
AWS Security Hub :
AWS Security Hub is a cloud security posture management service that provides a comprehensive view of security alerts and security posture across AWS accounts. It integrates with AWS services like GuardDuty, Inspector, and AWS Config, as well as other AWS Partner solutions, to collect security data and findings from multiple sources. Security Hub helps to prioritise security issues, conduct automated compliance checks against AWS best practices and industry standards, and enables automated remediation of identified issues. It provides a centralised view of the security alerts and compliance status, making it easier to identify and mitigate potential security risks across the AWS environment. Security Hub also supports custom controls and standards, allowing us to define and assess our own security requirements. By consolidating security findings and compliance data, Security Hub simplifies the process of managing the overall security and compliance posture in the AWS Cloud.
GuardDuty :
Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorised behavior to protect AWS accounts, workloads, and data. It analyzes various data sources, including AWS CloudTrail event logs, VPC Flow Logs, and DNS logs, using machine learning and threat intelligence to identify potential threats. GuardDuty can detect activities such as compromised EC2 instances, unauthorized deployments, cryptocurrency mining, data exfiltration attempts, and suspicious API calls or network traffic patterns. When GuardDuty detects a potential threat, it generates security findings that are visible through the GuardDuty console, AWS Security Hub, and Amazon CloudWatch Events. These findings provide detailed information about the threat, including its severity, type, and recommended remediation steps. GuardDuty integrates with other AWS services like AWS Lambda and Amazon CloudWatch to enable automated response and remediation actions based on the detected threats, helping to quickly mitigate risks and protect the AWS environment from potential attacks or compromises.
VPC :
AWS Virtual Private Cloud (VPC) is a logically isolated section of the Amazon Web Services (AWS) cloud, where one can launch AWS resources in a virtual network that is defined. A VPC allows control of the virtual networking environment, including the selection of IP address ranges, creation of subnets, configuration of route tables, and network gateways. Within a VPC, we provisioned resources such as Amazon Elastic Compute Cloud (EC2) instances, Elastic Load Balancing, Amazon Relational Database Service (RDS), and other AWS services. VPCs provide advanced security features like network access control lists (ACLs) and security groups, enabling control of the inbound and outbound traffic at the subnet and instance level. Additionally, we could establish encrypted connections between the corporate data center and the VPC through a Virtual Private Network (VPN) connection or an AWS Direct Connect private virtual interface, effectively extending the on-premises network to the AWS cloud.
AWS Snapshot :
An AWS Snapshot is an incremental backup of an Amazon Elastic Block Store (EBS) volume that captures the state of the volume at a particular point in time. Snapshots are stored in Amazon Simple Storage Service (S3), which provides durable and redundant data storage. AWS Snapshots are a crucial component of data protection and disaster recovery strategies, providing a reliable and efficient way to backup and restore EBS volumes in the AWS cloud environment.
External Service
Open VPN
OpenVPN is an open-source virtual private network (VPN) solution that provides secure and encrypted network access over the internet. It creates a secure tunnel between a client (such as a laptop or mobile device) and a VPN server, allowing users to access private networks and resources as if they were directly connected to the local network.
Outcomes
- With proper processes and safeguards we were able to Migrate the Application successfully to AWS
- Successful implementation for security services for ISO27000
- Implemented vertically scaling script for EC2 instance as per requirement
- Secure access through OpenVPN for Admin and Developer access.
- Successfully implemented Development and Production Odoo workload with security required as per the customer need.
At this manufacturing company, Electromech successfully implemented the Development and Production Odoo workload with security required as per the customer requirements..
